_______ _______ _ _______ _______ _______ _______ _
|\ /|( ____ \( ___ )| \ /\( ____ )( ___ )( ____ \( ____ \ / )
| ) ( || ( \/| ( ) || \ / /| ( )|| ( ) || ( \/| ( \/ _ / /
| | _ | || (__ | (___) || (_/ / | (____)|| (___) || (_____ | (_____ (_)( (
| |( )| || __) | ___ || _ ( | _____)| ___ |(_____ )(_____ ) | |
| || || || ( | ( ) || ( \ \ | ( | ( ) | ) | ) | _ ( (
| () () || (____/\| ) ( || / \ \| ) | ) ( |/\____) |/\____) | (_) \ \
(_______)(_______/|/ \||_/ \/|/ |/ \|\_______)\_______) \_)
weakpass is a basic script that automates the generation of weak and standardized passwords. Designed to be a simple but valuable tool during the initial phase of security tests.
go install github.com/phor3nsic/weakpass@latest
To get a list of options:
weakpass -h
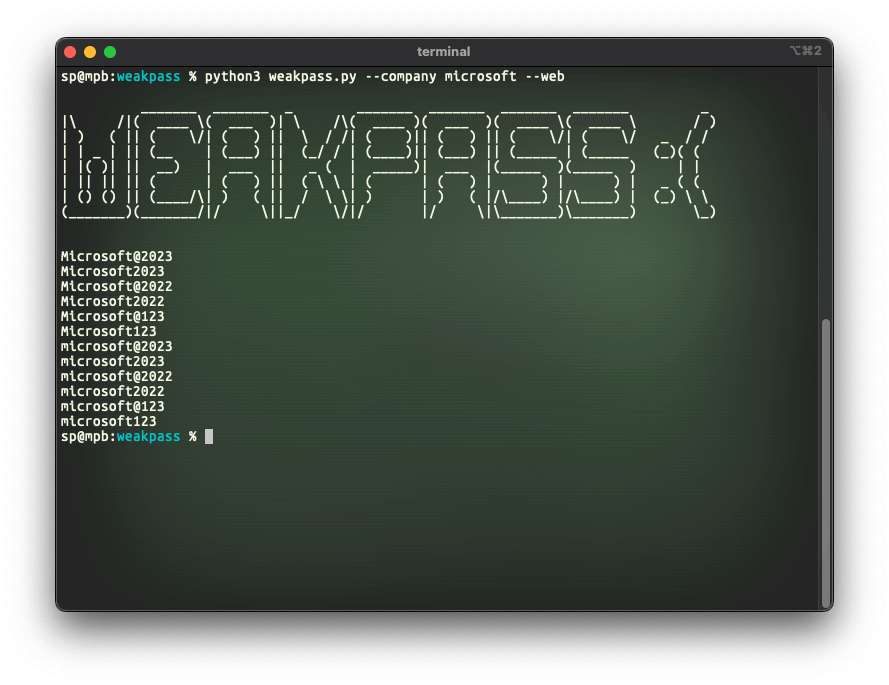
Example for a small list focused on a web spraying attack:
weakpass -c microsoft -w
Example for a big list focused on brute force cracking (eg: hashcat):
weakpass -c microsoft -b -o mscrack.txt
Example for multi companies:
weakpass -c microsoft,xbox,skype -b -o mscrack.txt