-
-
Notifications
You must be signed in to change notification settings - Fork 19
Usage
After installing the installation package generated for your system, you will be able to see airgorah in your applications list.

If you prefer to run it from the command line, you can do so by running:
pkexec airgorah
⚠️ If you are running on a linux distributionwithout systemd(Alpine,Void,Artix, ...), you may have to manually kill services that could interfere with network cards management before launching the application, for examplewpa_supplicantordhcpcd.
Before the launch of the application, you will be asked to enter your password (through pkexec). This is because airgorah needs to run as root to be able to manage the network interfaces and uses inner tools like aircrack-ng suite.
At the launch of the application, you will be presented with a list of the wireless network interfaces available on your system. You can select the one you want to use for future scans and attacks by clicking on it:

After selecting an interface:
- The chosen wireless card will be set to monitor mode
- If enabled in the settings, the network manager will be stopped
- If enabled in the settings, the MAC address of the wireless card will be changed
- The scan will then automatically start
You will be presented with a list of the wireless networks available around you:
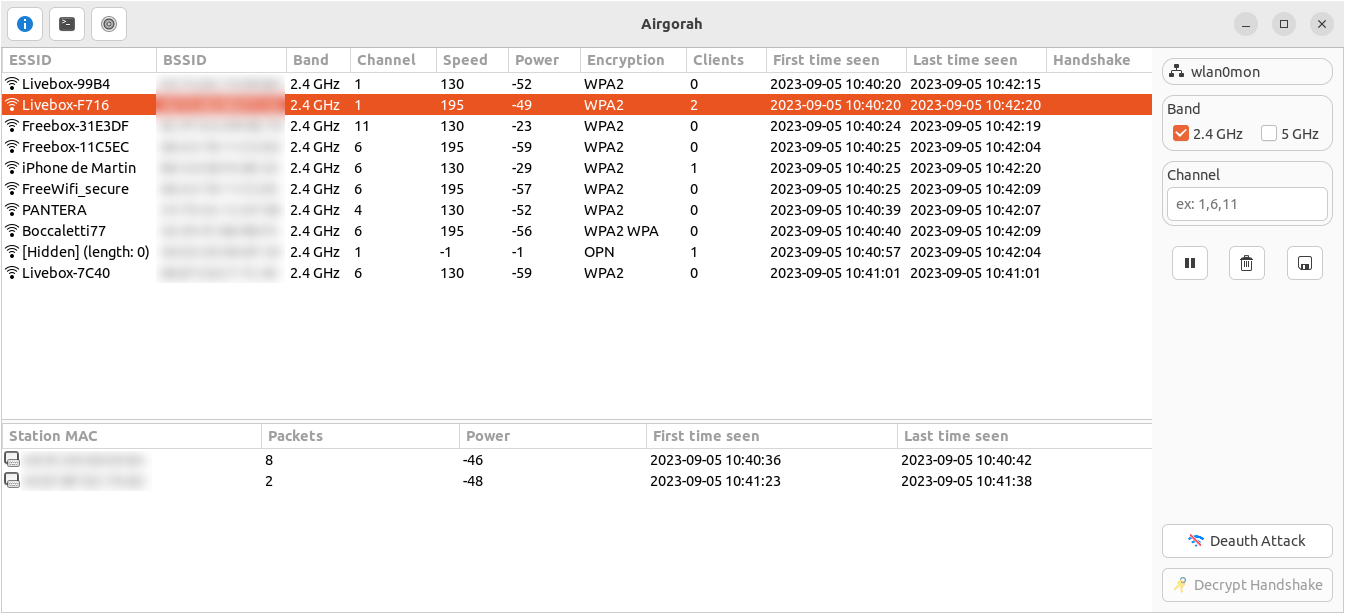

This list contains all the wireless networks available around you. It is updated in real time as new networks are detected. The data displayed is the parsed result of airodump-ng and is updated every second.
It is possible to sort the networks by clicking on the column headers.
This list contains all the clients connected to the selected wireless network.
It is possible to sort the clients by clicking on the column headers.
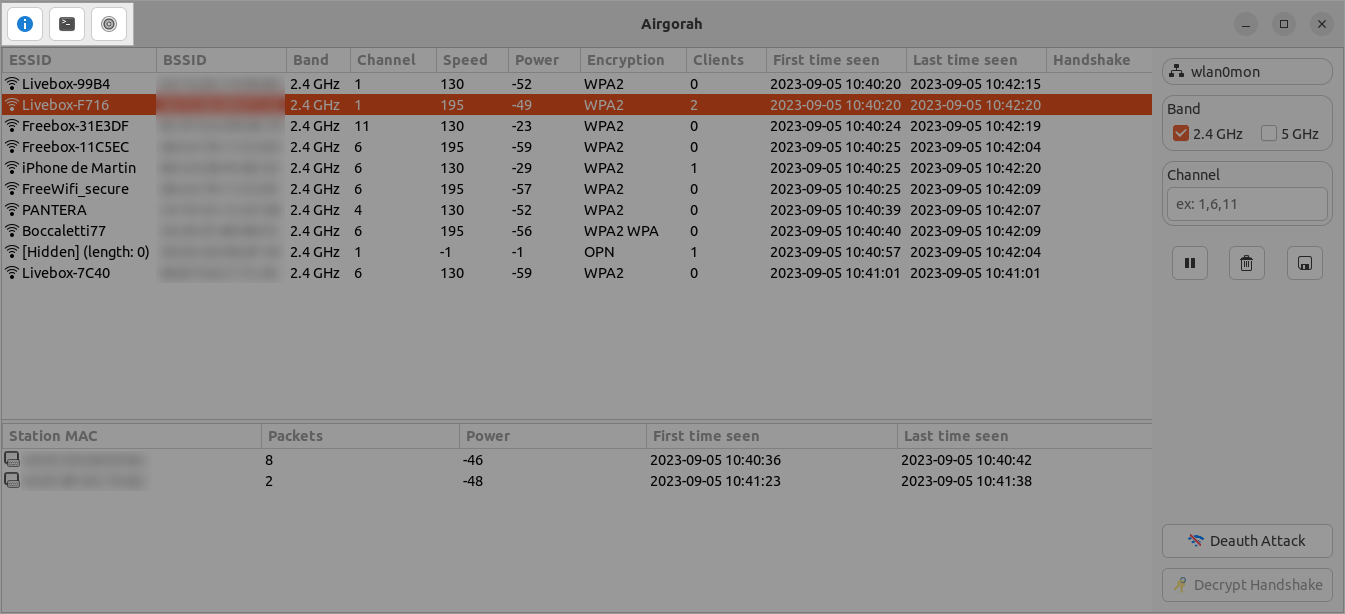 The header bar contains the following elements:
The header bar contains the following elements:
- The update button (only visible if an update is available)
- The about button
- The handshake decryption button
- The settings button
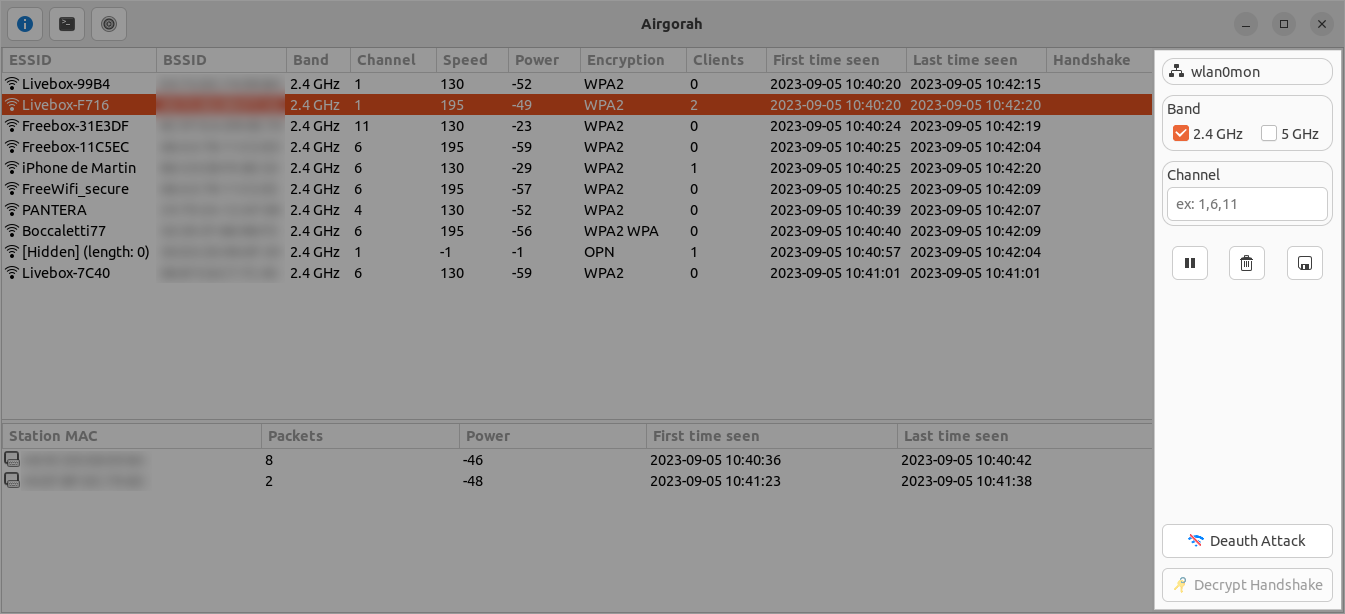
The right bar contains the following elements:
At the top:
- The selected interface name
- The band selector
You can select the bands you want to scan by checking the corresponding checkboxes. The scan settings will be updated in real time.
- The channel selector
If left empty, all the channels of the selected bands will be scanned:
2.4 GHz: 1-14
5 GHz: 36-165
If you want to scan only a few channels, you can enter the channel numbers separated by a comma. The scan settings will be updated in real time.
At the middle:
- The start/stop scan button
- The clear results button
- The save capture button
At the bottom:
- The deauth selected wifi button
To perform a deauth attack on the selected wifi, you can click on the deauth button. This will open a new window where you can select the clients you want to deauth.
- The decrypt selected wifi button
To decrypt the handshake of the selected wifi, you will need to capture the handshake first, then you will be able to click on the decrypt button. This will open a new window where you can select the wordlist or the bruteforce parameters to use to decrypt the password.
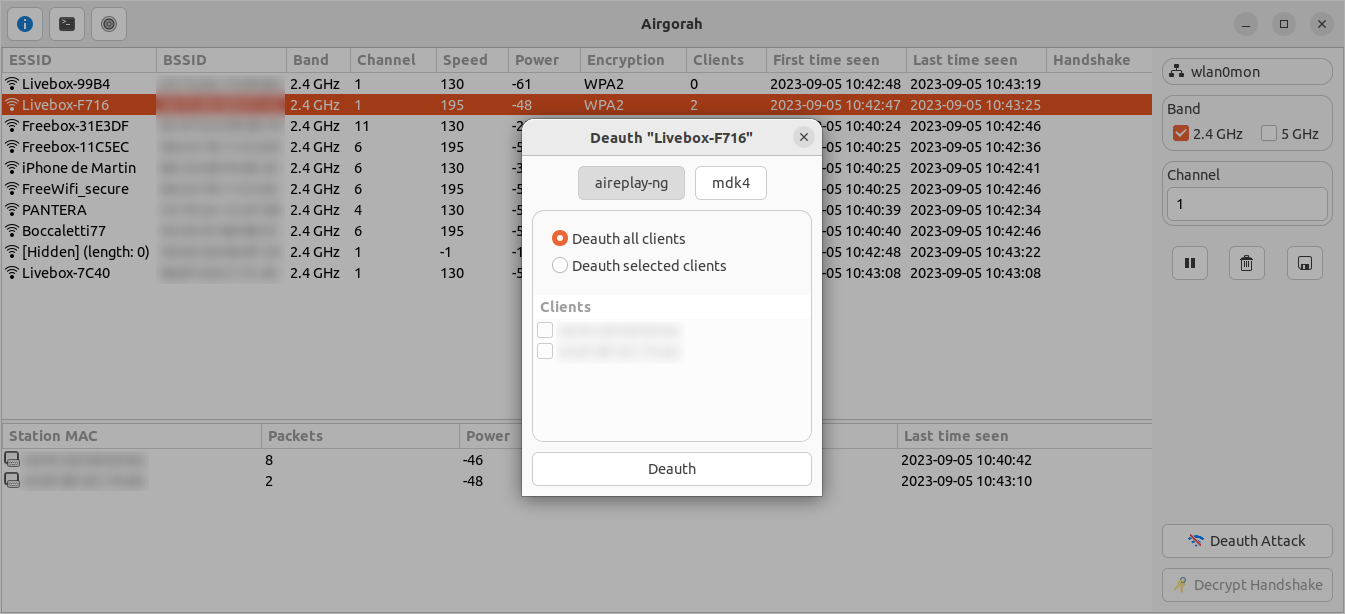
On this window, you can perform a deauth attack on the selected wifi network.
First, you can choose the backend software to use. You can choose between aireplay-ng and mdk4. The default is aireplay-ng.
Then, you can select the clients you want to deauth by clicking on the corresponding checkbox. You can also select Deauth all clients to perform a broadcast deauth attack (default).
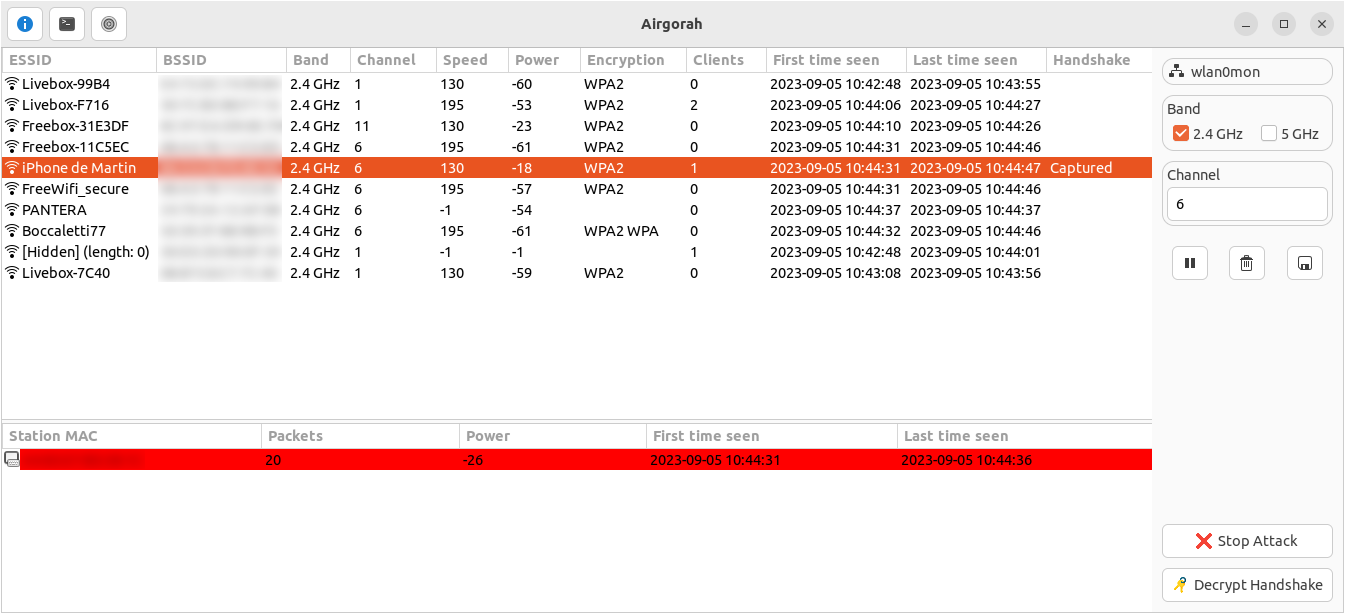
Once you clicked on the Deauth button, the deauth attack will start and the selected clients will be disconnected from the selected wifi network.
You can stop the attack at any time by clicking on the Stop Attack button at the bottom right.
Once clients reconnects to the wifi network, if a handshake is captured, it will be displayed on the handshake column of the wifi list.
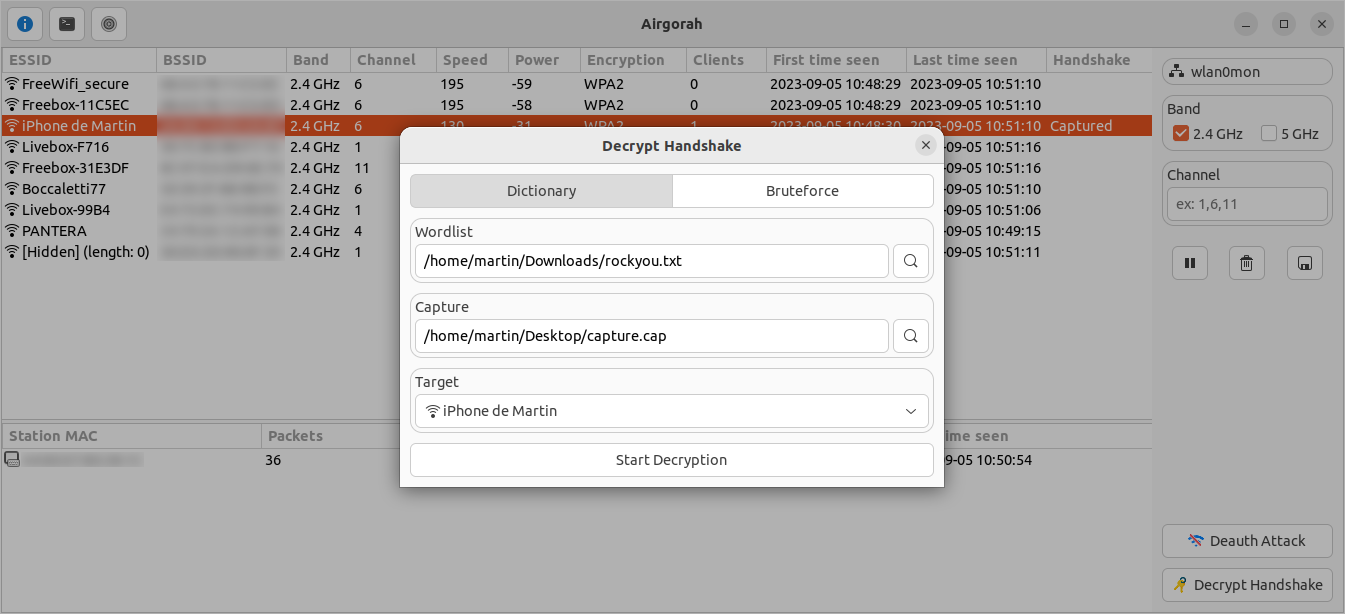
On this window, you can decrypt a handshake from a capture file.
You will need to select the capture file containing the handshake and the wifi network password you want to decrypt.
To perform the decryption, you can choose between a wordlist file or a selection of bruteforce parameters:
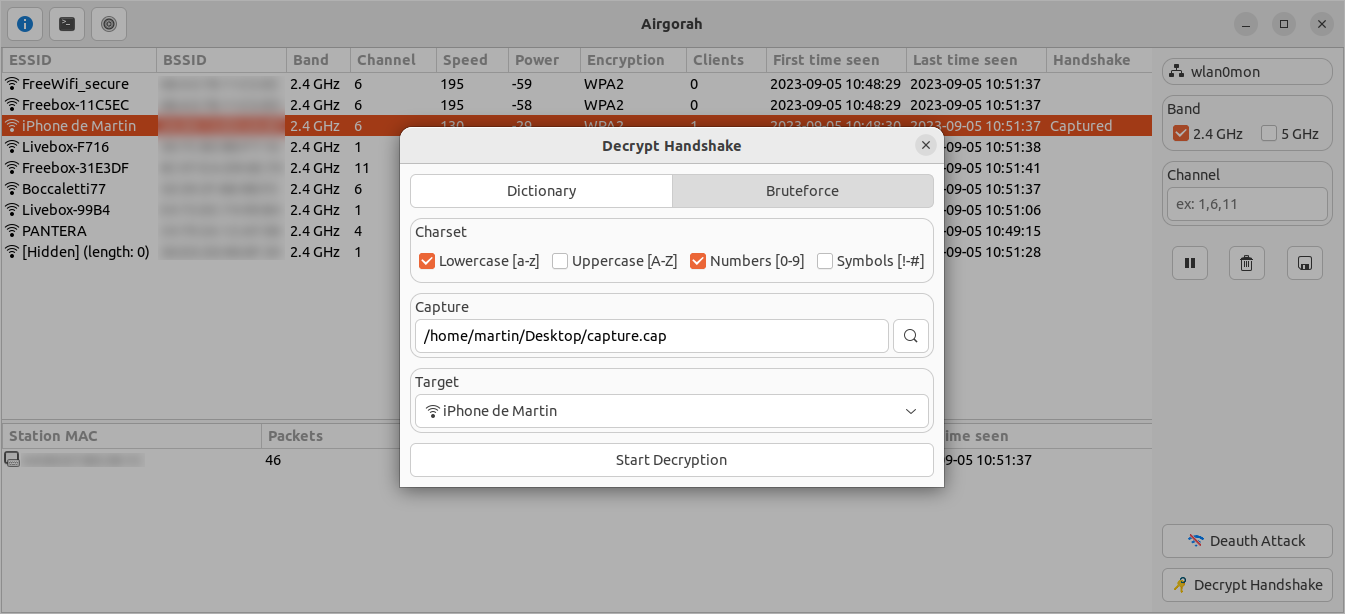
Once you clicked on the Start Decryption button, a separate terminal window will open and the decryption will start.
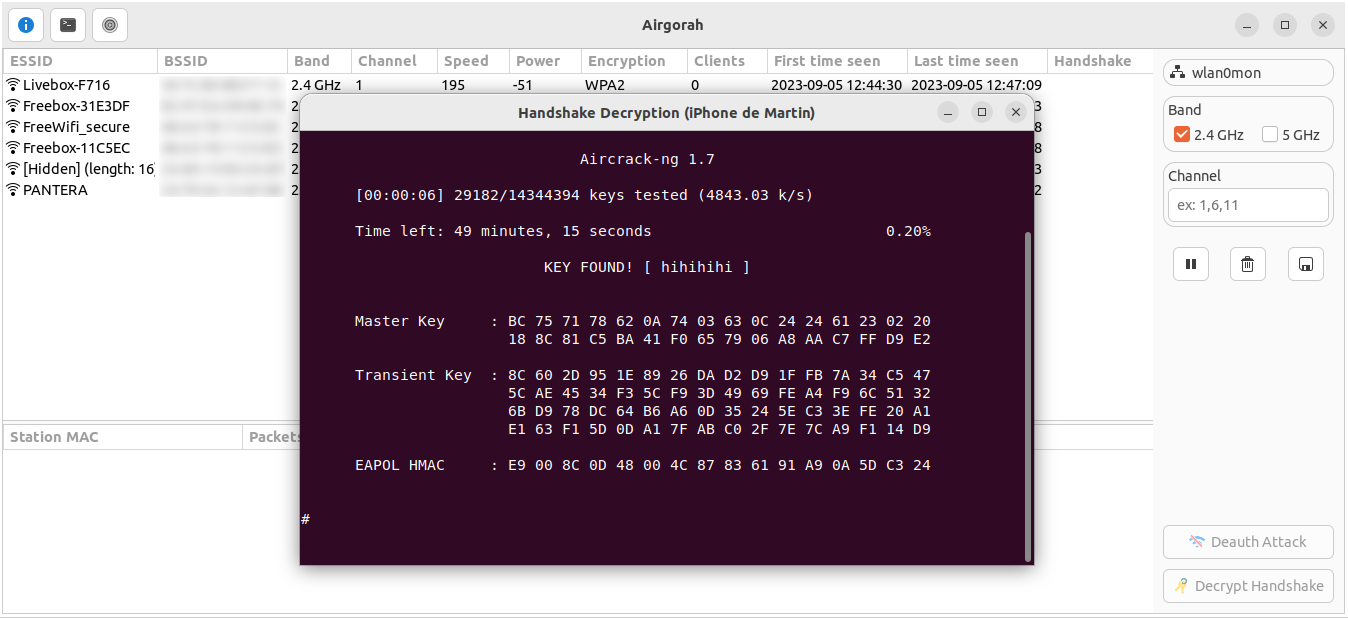
At this point, you can choose to close airgorah and the decryption will continue on the terminal window.
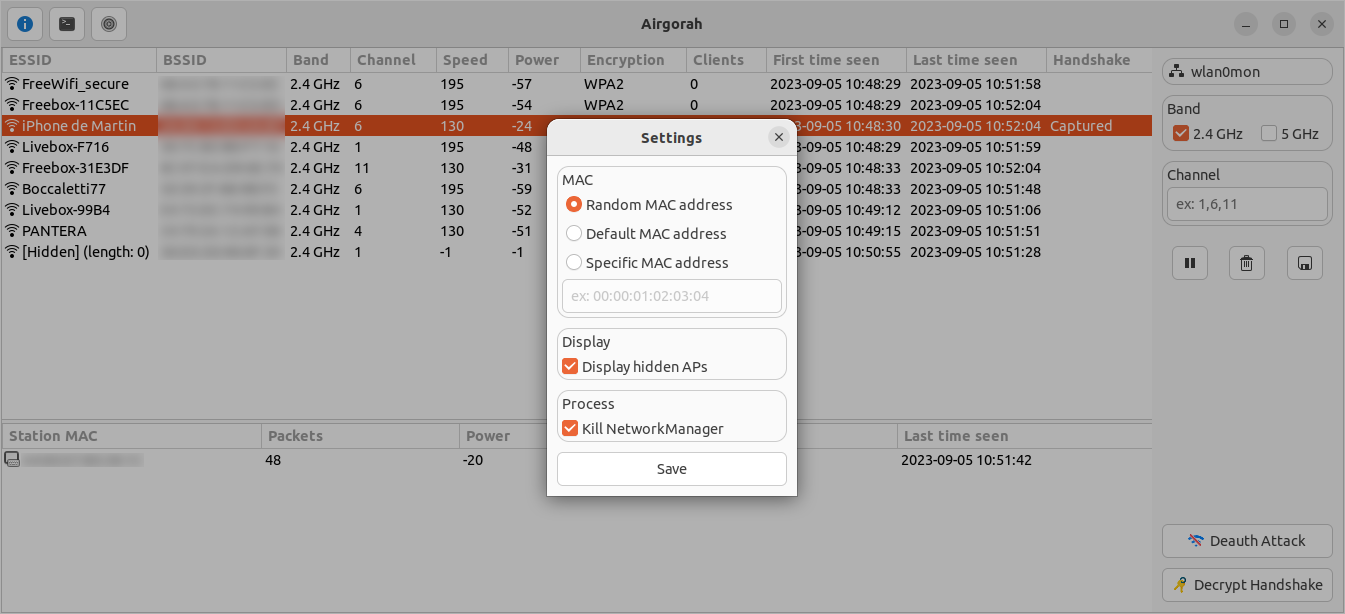
On this window, you can change the settings of airgorah.
The settings are saved in the /etc/airgorah/config.toml file.