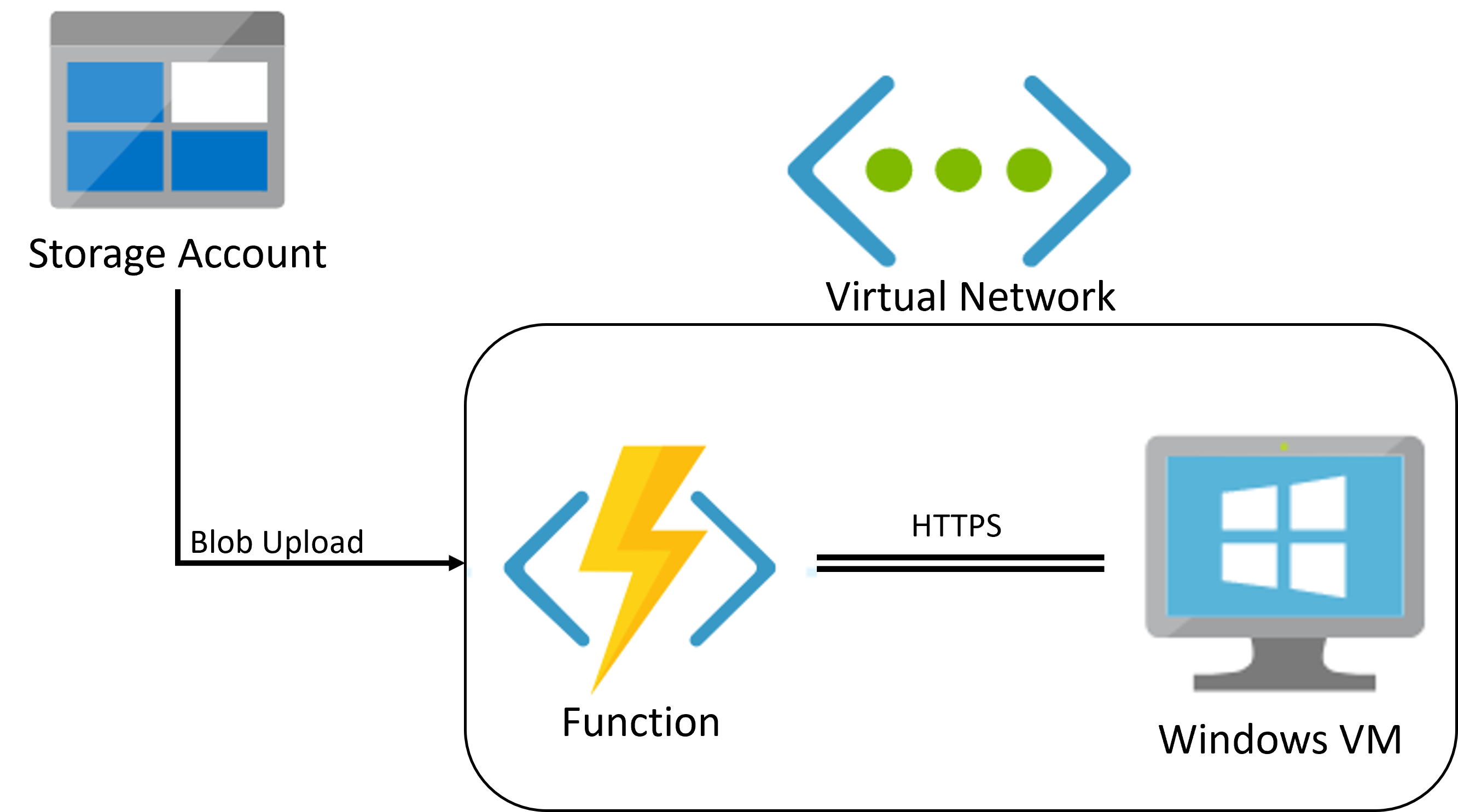
SFTP for Azure Storage with real-time antivirus scanning is an terraform template (converted from https://github.com/Azure/azure-storage-av-automation which is an ARM template) that provisions resources in your environment in order to protect an Azure blob container from malware by scanning every blob that’s uploaded via SFTP. The project consists of a function triggered when files are uploaded to or updated in a Blob storage container, and a Windows VM that utilizes Microsoft Defender Antivirus to scan the uploaded/updated files in real-time.
For each blob uploaded to the protected container, the function will send the blob to the VM for scanning and change the blob location according to the scan results:
- If the blob is clean, it’s moved to the clean-files container
- If it contains malware it’s moved to the quarantine-files container
The Azure function and the VM are connected through a virtual network and communicate using HTTPS requests.
List of created resources:
- Function App
- App Service Plan
- Virtual Network
- Network Security Group
- Storage Accounts - for the function app and SFTP
- Virtual Machine - for scanning the uploaded/updated files using Microsoft Defender Antivirus
- Disk - Storage for the VM
- Network Interface - NIC for the VM
zip folder - containing the function app zip file which will be uploaded to deployment-files container in AV storage account and used in WEBSITE_RUN_FROM_PACKAGE avsftp.tfvars.template - TFVARS template containing sample parameters values
- Use the following command to clone the repo
git clone https://github.com/jasonpanggit/terraform-azure-storage-sftp-av-automation.git - Rename avsftp.tfvars.template to avsftp.tfvars and change the necessary parameter values to whatever you need (Important: remember to set the expiry date of the SAS token used for function app deployment to something short like a day or even shorted than that)
- Go to SFTP storage account resource in Azure portal, open SFTP blade, enable SFTP, add the new-files container and other containers (e.g. quarantine-files, clean-files) if you want, set the necessary access permissions to the container(s) added, set the home directory to "new-files" and add local user with SSH password/key (Note: if you are using SSH password, copy the password generated into Notepad before closing the window because you won't be able to retrieve it again and will need to re-generate it again)
- Enable App Insights in Function App (optional) if you want
- Open WinSCP and enter the credentials (SSH password/key) and upload a virus file into the new-files container ()to test it out (Note: if you are using SSH key, you can use PuttyGEN to convert the PEM file generated in Azure to PPK file which most SFTP client uses)
- Enabling SFTP (need to manually enable it in Azure Portal) and adding local users
- Saving storage access details in Azure Key Vault (MSI cannot be used in function app because key vault access policy creation requires function app to be created first in order to get the object id)
- This repository is based on https://github.com/Azure/azure-storage-av-automation which is using ARM template.
- My repo for ScanUploadedBlobFunction which fixed some HTTP client bugs in the above repo which cause access restriction - https://github.com/jasonpanggit/scan-uploaded-blob-function
- My repo for ScanHTTPServer which is running in the VM waiting to scan the uploaded file - https://github.com/jasonpanggit/scan-http-server