diff --git a/README.md b/README.md
index 407b2ad..ade730c 100644
--- a/README.md
+++ b/README.md
@@ -4,166 +4,37 @@ This [repository](https://github.com/ddosify/ddosify-helm-charts) hosts the Helm
There are two charts available in this repository:
-- 🏠 [Ddosify Self-Hosted Chart](#ddosify-self-hosted-chart)
+- 🏠 [Ddosify Platform Self-Hosted Chart](#ddosify-platform-self-hosted-chart)
- 🐝 [Alaz Chart - Ddosify eBPF Agent](#alaz-chart---ddosify-ebpf-agent)
## What is Ddosify?
-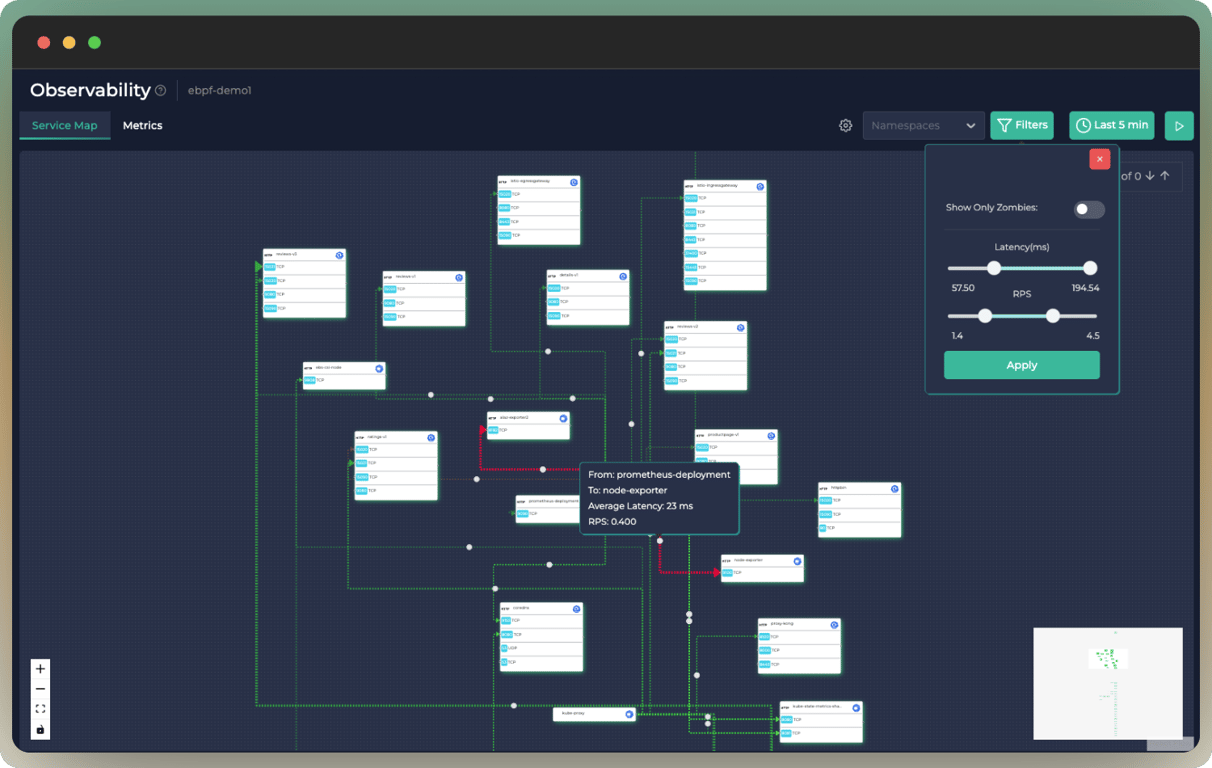 +
+ +Ddosify automatically generates Service Map of your K8s cluster without code instrumentation or sidecars with eBPF. So you can easily find the bottlenecks in your system. Red lines indicate the high latency between services.
+Ddosify automatically generates Service Map of your K8s cluster without code instrumentation or sidecars with eBPF. So you can easily find the bottlenecks in your system. Red lines indicate the high latency between services.
-Ddosify is a comprehensive performance testing and observability platform. It consists of the following components:
-
-- ⚡️ [Ddosify Engine](https://github.com/ddosify/ddosify/blob/master/engine_docs/README.md): High-performance, single engine load testing tool.
-- 🏠 [Ddosify Self-Hosted](https://github.com/ddosify/ddosify/tree/master/selfhosted): Self-hosted, distributed load testing and observability platform.
-- ☁️ [Ddosify Cloud](https://app.ddosify.com): Cloud-based, distributed load testing and observability platform.
-- 🐝 [Alaz](https://github.com/ddosify/alaz): Ddosify eBPF agent for Kubernetes. It can inspect and collect Kubernetes (K8s) service traffic without the need for code instrumentation, sidecars, or service restarts. It also gets system information and resources (CPU, Memory, Disk and Network) via the Prometheus Node Exporter.
+Ddosify is an [open-source](https://github.com/ddosify/ddosify) Kubernetes Monitoring and Performance Testing platform.
## Pre-requisites
- Kubernetes 1.19+
- [Helm](https://helm.sh/docs/intro/install/) must be installed to use the Ddosify charts.
-## Ddosify Self-Hosted Chart
-
-[Ddosify Self-Hosted](https://github.com/ddosify/ddosify/tree/master/selfhosted) features a web-based user interface, distributed load generation, and **Kubernetes Monitoring** capabilities. While it shares many of the same functionalities as Ddosify Cloud, the Self-Hosted version is designed to be deployed within your own infrastructure for enhanced control and customization.
-
-To install the Ddosify Self-Hosted chart via Helm, run the following commands:
-
-```bash
-helm repo add ddosify https://ddosify.github.io/ddosify-helm-charts/
-helm repo update
-kubectl create namespace ddosify
-helm upgrade --install --namespace ddosify ddosify ddosify/ddosify --wait
-```
-
-### Accessing the Ddosify Dashboard (Port Forwarding)
-
-Port forward the Ddosify nginx reverse proxy service to access the Ddosify dashboard:
-
-```bash
-LOCAL_PORT=8014
-kubectl port-forward --namespace ddosify service/nginx-service $LOCAL_PORT:80
-```
-
-Open the browser and navigate to http://localhost:8014.
-
-### Upgrading the Ddosify Chart
-
-To upgrade the Ddosify chart, run the following commands:
-
-```bash
-helm repo add ddosify https://ddosify.github.io/ddosify-helm-charts/
-helm repo update
-helm upgrade --namespace ddosify ddosify ddosify/ddosify --wait
-```
+## Ddosify Platform Self-Hosted Chart
-### Add New Engine (Optional):
+With the Ddosify Self-Hosted chart, you can deploy the Ddosify platform to your Kubernetes cluster.
-Currently, the Ddosify chart deploys a single engine (load generator). To add more engines, you can upgrade the chart with the desired number of engine count as follows. Before adding new engines, ensure that you have enabled the distributed mode by clicking the `Unlock the Distributed Mode` button in the Ddosify UI.
+Check the [Ddosify Self-Hosted](./charts/ddosify/README.md) chart for the installation and configuration details.
-```bash
-ENGINE_COUNT=3
-helm upgrade --namespace ddosify ddosify ddosify/ddosify --set hammerReplicas=$ENGINE_COUNT --wait
-```
-### External Database (Optional):
-
-By default, the Ddosify chart deploys a PostgreSQL and InfluxDB. If you want to use them externally, you can write a custom values file (`values-external_db.yaml`) as follows:
-
-```yaml
-influxDB:
- external: true
- url: "https://us-east-1-1.aws.cloud2.influxdata.com"
- apiToken: ""
- org: ""
-
-postgres:
- external: true
- host: "postgres-rds-test.xxxxxx.rds.amazonaws.com"
- port: 5432
- username: "postgres"
- password: ""
-```
-
-In this example, we are using the external InfluxDB Cloud and AWS RDS PostgreSQL. You must change the values according to your setup. Note that the external database must be accessible from the Kubernetes cluster. Then, you can install the chart with the custom values file as follows:
-
-```bash
-helm upgrade --install --namespace ddosify ddosify ddosify/ddosify --values values-external_db.yaml --wait
-```
-
-The recommended and tested version of PostgreSQL is `13.6` and InfluxDB is `2.6.1`. If you get any errors on different versions, please open an issue. We will try to fix it as soon as possible. To avoid the latency, the external databases should be as close as possible to the Kubernetes cluster.
-
-### Cleanup
-
-```bash
-helm delete ddosify --namespace ddosify
-```
-
-### Telemetry Data
+## Alaz Chart - Ddosify eBPF Agent
-Ddosify collects telemetry data to improve the product. You can disable it by setting the `ANONYMOUS_TELEMETRY_ENABLED` environment variable to `False` in the [backend](./charts/ddosify/templates/backend.yaml) deployment.
+With the Alaz chart, you can deploy the Ddosify eBPF agent to your Kubernetes cluster that you want to monitor. Alaz sends the collected data to the Ddosify platform.
-```yaml
-...
-env:
- - name: ANONYMOUS_TELEMETRY_ENABLED
- value: "False"
-...
-```
+Check the [Alaz](./charts/alaz/README.md) chart for the installation and configuration details.
-Check the example telemetry data that Ddosify collects from [here](https://github.com/ddosify/ddosify/tree/master/selfhosted#example-data).
-## Alaz Chart - Ddosify eBPF Agent
+## Communication
-[Alaz](https://github.com/ddosify/alaz) is an open-source Ddosify eBPF agent that can inspect and collect Kubernetes (K8s) service traffic without the need for code instrumentation, sidecars, or service restarts. This is possible due to its use of eBPF technology. Alaz can create a Service Map that helps identify golden signals and problems like high latencies, 5xx errors, zombie services, SQL queries. Additionally, it can gather system information and resources via the Prometheus Node Exporter, which is readily available on the agent.
-
-To install the Alaz chart, first, you need to add the Ddosify Helm repository:
-
-```bash
-helm repo add ddosify https://ddosify.github.io/ddosify-helm-charts/
-helm repo update
-```
-
-Then, you can install the Alaz chart with the following command:
-```bash
-# Replace with your monitoring ID from the Ddosify UI. Change XXXXX with your monitoring ID.
-MONITORING_ID=XXXXX
-# Set BACKEND_HOST with your Ddosify Self-Hosted Endpoint. If your Ddosify Self-Hosted endpoint is http://localhost:8014, then BACKEND_HOST=http://localhost:8014/api
-BACKEND_HOST=XXXXX
-helm repo add ddosify https://ddosify.github.io/ddosify-helm-charts/
-helm repo update
-kubectl create namespace ddosify
-helm upgrade --install --namespace ddosify alaz ddosify/alaz --set monitoringID=$MONITORING_ID --set backendHost=$BACKEND_HOST
-```
-
-For more installation methods, see [Alaz (Ddosify eBPF Agent)](https://github.com/ddosify/alaz).
-
-### Alaz Parameters
-
-The following table lists the configurable parameters of the Alaz chart and their default values.
-
-| Parameter | Description | Type | Default |
-| --- | --- | --- | --- |
-| `monitoringID` | **CHANGE**: Monitoring ID (required). You can get it from Ddosify UI, Cluster Detail Page. | string | `` |
-| `backendHost` | Backend host URL to send the collected data. Default is [Ddosify Cloud](https://app.ddosify.com/). If you have Ddosify Self-Hosted installed, you can give the backend URL. | string | `https://api.ddosify.com:443` |
-| `namespace` | Namespace to deploy the chart | string | `ddosify` |
-| `logLevel` | [Zero log](https://github.com/rs/zerolog) level (0: trace, 1: debug, 2: info, 3: warn, 4: error, 5: fatal, 6: panic) | int | `1` |
-| `resources.limits.cpu` | CPU limit | string | `1` |
-| `resources.limits.memory` | Memory limit | string | `1Gi` |
-| `resources.requests.cpu` | CPU request | string | `500m` |
-| `resources.requests.memory` | Memory request | string | `400Mi` |
-| `image` | Alaz Docker image | string | `ddosify/alaz:v0.1.4` |
-| `imagePullPolicy` | Image pull policy | string | `IfNotPresent` |
-| `containerPort` | Container port for debugging and profiling Alaz | int | `8181` |
-| `podAnnotations` | Annotations to add to the pod | object | `{}` |
-| `metricsEnabled` | Enable prometheus node exporter metrics (cpu, memory, network, disk, etc.) | bool | `true` |
-| `serviceMapEnabled` | Enable service map for K8s network traffic using eBPF | bool | `true` |
-| `distTracingEnabled` | Enable distributed tracing using eBPF | bool | `true` |
-
-You can override these default values by creating a `values.yaml` file and specifying your own values or using the `--set` flag during installation.
-
-## Notes
-
-- For AWS EKS, Amazon EKS CSI Driver addon must be enabled to use the EBS storage class. For more information, see [Amazon EKS CSI Driver](https://docs.aws.amazon.com/eks/latest/userguide/ebs-csi.html).
+You can join our [Discord Server](https://discord.gg/9KdnrSUZQg) for discussions, support, and community updates.
diff --git a/assets/ddosify_service_map.png b/assets/ddosify_service_map.png
new file mode 100644
index 0000000..90f943d
Binary files /dev/null and b/assets/ddosify_service_map.png differ
diff --git a/charts/alaz/Chart.yaml b/charts/alaz/Chart.yaml
index 0497e5f..b601611 100644
--- a/charts/alaz/Chart.yaml
+++ b/charts/alaz/Chart.yaml
@@ -1,6 +1,6 @@
apiVersion: v2
name: alaz
-description: Alaz is an open-source Ddosify eBPF agent that can inspect and collect Kubernetes (K8s) service traffic without the need for code instrumentation, sidecars, or service restarts. This is possible due to its use of eBPF technology. Alaz can create a Service Map that helps identify golden signals and problems like high latencies, 5xx errors, zombie services, SQL queries. Additionally, it can gather system information and resources via the Prometheus Node Exporter, which is readily available on the agent.
+description: Alaz is an open-source Ddosify eBPF agent that can inspect and collect Kubernetes (K8s) service traffic without the need for code instrumentation, sidecars, or service restarts. Alaz can create a Service Map that helps identify golden signals and problems like high latencies, 5xx errors, zombie services, SQL queries. Additionally, it can gather system information and resources via the Prometheus Node Exporter, which is readily available on the agent.
# A chart can be either an 'application' or a 'library' chart.
#
@@ -16,12 +16,16 @@ icon: https://d2uj9largygsoq.cloudfront.net/docker/ddosify-square-icon-db.svg
# This is the chart version. This version number should be incremented each time you make changes
# to the chart and its templates, including the app version.
# Versions are expected to follow Semantic Versioning (https://semver.org/)
-version: 0.5.1
+version: 0.5.2
# This is the version number of the application being deployed. This version number should be
# incremented each time you make changes to the application. Versions are not expected to
# follow Semantic Versioning. They should reflect the version the application is using.
# It is recommended to use it with quotes.
-appVersion: "v0.5.0"
+appVersion: "v0.5.2"
kubeVersion: ">=1.16.0-0"
+
+annotations:
+ charts.openshift.io/name: "Alaz is an open-source Ddosify eBPF agent that can inspect and collect Kubernetes (K8s) service traffic without the need for code instrumentation, sidecars, or service restarts. Alaz can create a Service Map that helps identify golden signals and problems like high latencies, 5xx errors, zombie services, SQL queries. Additionally, it can gather system information and resources via the Prometheus Node Exporter, which is readily available on the agent."
+ charts.openshift.io/versions: ">=4.5"
diff --git a/charts/alaz/README.md b/charts/alaz/README.md
new file mode 100644
index 0000000..9b1eee7
--- /dev/null
+++ b/charts/alaz/README.md
@@ -0,0 +1,48 @@
+# Alaz Chart - Ddosify eBPF Agent
+
+[Alaz](https://github.com/ddosify/alaz) is an open-source Ddosify eBPF agent that can inspect and collect Kubernetes (K8s) service traffic without the need for code instrumentation, sidecars, or service restarts. This is possible due to its use of eBPF technology. Alaz can create a Service Map that helps identify golden signals and problems like high latencies, 5xx errors, zombie services, SQL queries. Additionally, it can gather system information and resources via the Prometheus Node Exporter, which is readily available on the agent.
+
+To install the Alaz chart, first, you need to add the Ddosify Helm repository:
+
+```bash
+helm repo add ddosify https://ddosify.github.io/ddosify-helm-charts/
+helm repo update
+```
+
+Then, you can install the Alaz chart with the following command:
+```bash
+# Replace with your monitoring ID from the Ddosify UI. Change XXXXX with your monitoring ID.
+MONITORING_ID=XXXXX
+# Set BACKEND_HOST with your Ddosify Self-Hosted Endpoint. If your Ddosify Self-Hosted endpoint is http://localhost:8014, then BACKEND_HOST=http://localhost:8014/api
+BACKEND_HOST=XXXXX
+helm repo add ddosify https://ddosify.github.io/ddosify-helm-charts/
+helm repo update
+kubectl create namespace ddosify
+helm upgrade --install --namespace ddosify alaz ddosify/alaz --set monitoringID=$MONITORING_ID --set backendHost=$BACKEND_HOST
+```
+
+For more installation methods, see [Alaz (Ddosify eBPF Agent)](https://github.com/ddosify/alaz).
+
+## Alaz Chart Configuration Parameters
+
+The following table lists the configurable parameters of the Alaz chart and their default values.
+
+| Parameter | Description | Type | Default |
+| --- | --- | --- | --- |
+| `monitoringID` | **CHANGE**: Monitoring ID (required). You can get it from Ddosify UI, Cluster Detail Page. | string | `""` |
+| `backendHost` | Backend host URL to send the collected data. Default is [Ddosify Cloud](https://app.ddosify.com/). If you have Ddosify Self-Hosted installed, you can give the backend URL. | string | `https://api.ddosify.com:443` |
+| `namespace` | Namespace to deploy the chart | string | `ddosify` |
+| `logLevel` | [Zero log](https://github.com/rs/zerolog) level (0: trace, 1: debug, 2: info, 3: warn, 4: error, 5: fatal, 6: panic) | int | `1` |
+| `resources.limits.cpu` | CPU limit | string | `1` |
+| `resources.limits.memory` | Memory limit | string | `1Gi` |
+| `resources.requests.cpu` | CPU request | string | `500m` |
+| `resources.requests.memory` | Memory request | string | `400Mi` |
+| `image` | Alaz Docker image | string | - |
+| `imagePullPolicy` | Image pull policy | string | `IfNotPresent` |
+| `containerPort` | Container port for debugging and profiling Alaz | int | `8181` |
+| `podAnnotations` | Annotations to add to the pod | object | `{}` |
+| `metricsEnabled` | Enable prometheus node exporter metrics (cpu, memory, network, disk, etc.) | bool | `true` |
+| `serviceMapEnabled` | Enable service map for K8s network traffic using eBPF | bool | `true` |
+| `distTracingEnabled` | Enable distributed tracing using eBPF | bool | `true` |
+
+You can override these default values by creating a `values.yaml` file and specifying your own values or using the `--set` flag during installation.
diff --git a/charts/alaz/templates/tests/test-alaz.yaml b/charts/alaz/templates/tests/test-alaz.yaml
new file mode 100644
index 0000000..fea1a9a
--- /dev/null
+++ b/charts/alaz/templates/tests/test-alaz.yaml
@@ -0,0 +1,15 @@
+apiVersion: v1
+kind: Pod
+metadata:
+ name: "{{ include "alaz.fullname" . }}-test-api"
+ namespace: {{ .Values.namespace }}
+ annotations:
+ "helm.sh/hook": test
+ "helm.sh/hook-delete-policy": hook-succeeded,hook-failed
+spec:
+ serviceAccountName: alaz-serviceaccount
+ containers:
+ - name: test
+ image: bitnami/kubectl
+ command: ['kubectl', 'get', 'pods', '-l', 'app.kubernetes.io/name={{ include "alaz.name" . }}', '-o', 'jsonpath={..status.conditions[?(@.type=="Ready")].status}']
+ restartPolicy: Never
diff --git a/charts/alaz/values.schema.json b/charts/alaz/values.schema.json
new file mode 100644
index 0000000..9c9a8e5
--- /dev/null
+++ b/charts/alaz/values.schema.json
@@ -0,0 +1,103 @@
+{
+ "$schema": "http://json-schema.org/draft-07/schema#",
+ "title": "Alaz Helm Chart Values",
+ "description": "Validation schema for values of Alaz Helm chart",
+ "type": "object",
+ "properties": {
+ "namespace": {
+ "type": "string",
+ "description": "Namespace to deploy the chart",
+ "default": "ddosify"
+ },
+ "backendHost": {
+ "type": "string",
+ "format": "uri",
+ "description": "Backend host URL to send the collected data",
+ "default": "https://api.ddosify.com:443"
+ },
+ "monitoringID": {
+ "type": "string",
+ "description": "Monitoring ID (required). You can get it from Ddosify Platform"
+ },
+ "logLevel": {
+ "type": "integer",
+ "description": "Zero log level",
+ "enum": [0, 1, 2, 3, 4, 5, 6],
+ "default": 1
+ },
+ "resources": {
+ "type": "object",
+ "properties": {
+ "limits": {
+ "type": "object",
+ "properties": {
+ "cpu": {
+ "type": "string",
+ "pattern": "^\\d+m?$",
+ "default": "1"
+ },
+ "memory": {
+ "type": "string",
+ "pattern": "^\\d+(Mi|Gi)$",
+ "default": "1Gi"
+ }
+ }
+ },
+ "requests": {
+ "type": "object",
+ "properties": {
+ "cpu": {
+ "type": "string",
+ "pattern": "^\\d+m?$",
+ "default": "500m"
+ },
+ "memory": {
+ "type": "string",
+ "pattern": "^\\d+(Mi|Gi)$",
+ "default": "400Mi"
+ }
+ }
+ }
+ }
+ },
+ "image": {
+ "type": "string",
+ "description": "Alaz Docker image",
+ "default": "ddosify/alaz:v0.1.4"
+ },
+ "imagePullPolicy": {
+ "type": "string",
+ "enum": ["Always", "Never", "IfNotPresent"],
+ "default": "IfNotPresent"
+ },
+ "containerPort": {
+ "type": "integer",
+ "description": "Container port for debugging and profiling Alaz",
+ "default": 8181
+ },
+ "podAnnotations": {
+ "type": "object",
+ "additionalProperties": {
+ "type": "string"
+ },
+ "default": {}
+ },
+ "metricsEnabled": {
+ "type": "boolean",
+ "description": "Enable Prometheus node exporter metrics",
+ "default": true
+ },
+ "serviceMapEnabled": {
+ "type": "boolean",
+ "description": "Enable service map for K8s network traffic using eBPF",
+ "default": true
+ },
+ "distTracingEnabled": {
+ "type": "boolean",
+ "description": "Enable distributed tracing using eBPF",
+ "default": true
+ }
+ },
+ "required": ["namespace", "backendHost", "monitoringID", "logLevel", "resources", "image", "imagePullPolicy", "containerPort", "metricsEnabled", "serviceMapEnabled", "distTracingEnabled"]
+ }
+
\ No newline at end of file
diff --git a/charts/alaz/values.yaml b/charts/alaz/values.yaml
index af4c1a8..732330f 100644
--- a/charts/alaz/values.yaml
+++ b/charts/alaz/values.yaml
@@ -1,7 +1,7 @@
namespace: ddosify
backendHost: https://api.ddosify.com:443
-monitoringID: # required
+monitoringID: "" # required
logLevel: 1 # zero log levels: -1: trace, 0: debug, 1: info, 2: warn, 3: error, 4: fatal, 5: panic
resources:
@@ -12,7 +12,7 @@ resources:
cpu: 500m
memory: 400Mi
-image: ddosify/alaz:v0.5.0
+image: ddosify/alaz:v0.5.2
imagePullPolicy: IfNotPresent
containerPort: 8181
podAnnotations: {}
diff --git a/charts/ddosify/README.md b/charts/ddosify/README.md
new file mode 100644
index 0000000..ff5c741
--- /dev/null
+++ b/charts/ddosify/README.md
@@ -0,0 +1,126 @@
+# Ddosify Self-Hosted Chart
+
+[Ddosify Self-Hosted](https://github.com/ddosify/ddosify/tree/master/selfhosted) features a web-based user interface, distributed load generation, and **Kubernetes Monitoring** capabilities. While it shares many of the same functionalities as Ddosify Cloud, the Self-Hosted version is designed to be deployed within your own infrastructure for enhanced control and customization.
+
+To install the Ddosify Self-Hosted chart via Helm, run the following commands:
+
+```bash
+helm repo add ddosify https://ddosify.github.io/ddosify-helm-charts/
+helm repo update
+kubectl create namespace ddosify
+helm upgrade --install --namespace ddosify ddosify ddosify/ddosify --wait
+```
+
+## Accessing the Ddosify Dashboard (Port Forwarding)
+
+Port forward the Ddosify nginx reverse proxy service to access the Ddosify dashboard:
+
+```bash
+LOCAL_PORT=8014
+kubectl port-forward --namespace ddosify service/nginx-service $LOCAL_PORT:80
+```
+
+Open the browser and navigate to http://localhost:8014.
+
+## Upgrading the Ddosify Chart
+
+To upgrade the Ddosify chart, run the following commands:
+
+```bash
+helm repo add ddosify https://ddosify.github.io/ddosify-helm-charts/
+helm repo update
+helm upgrade --namespace ddosify ddosify ddosify/ddosify --wait
+```
+
+## Ddosify Chart Configuration Parameters
+
+The following table lists the configurable parameters of the Ddosify chart and their default values.
+
+| Parameter | Description | Type | Default |
+|-----------|-------------|------|---------|
+| `ingress.enabled` | Enable or disable ingress. | boolean | `false` |
+| `ingress.className` | Define the ingress class name like `nginx` or `kong`. | string | `""` |
+| `ingress.annotations` | Annotations for the ingress, can include multiple comments for configuration. | object | `{}` |
+| `ingress.hosts` | List of hosts for ingress, each with specific paths and pathTypes. | array | `[{"host": "ddosify.local", "paths": [{"path": "/", "pathType": "Prefix"}]}]` |
+| `ingress.tls` | TLS configuration for ingress. Uncomment and configure as needed. | array | `[]` |
+| `hammerReplicas` | Number of replicas for the hammer (load generator) service. If you want to increase the engine size for performance testing, increase this value. | integer | `1` |
+| `service.name` | The name of the outside service. You can forward the traffic with `kubectl port-forward` command to access the Ddosify dashboard. | string | `"nginx-service"` |
+| `service.port` | Port number the outside service operates on. | integer | `80` |
+| `influxDB.external` | Determines if InfluxDB is externally managed. | boolean | `false` |
+| `influxDB.url` | URL for InfluxDB, required if `external` is `true`. | string | `"http://influxdb:8086"` |
+| `influxDB.apiToken` | API token for InfluxDB, required if `external` is `true`. | string | `"5yR2qD5zCqqvjwCKKXojnPviQaB87w9JcGweVChXkhWRL"` |
+| `influxDB.org` | Organization for InfluxDB, required if `external` is `true`. | string | `"ddosify"` |
+| `influxDB.username` | InfluxDB username, used only if `external` is `false`. | string | `"admin"` |
+| `influxDB.password` | InfluxDB password, used only if `external` is `false`. | string | `"ChangeMe"` |
+| `postgres.external` | Determines if the Postgres server is externally managed. | boolean | `false` |
+| `postgres.host` | Host for Postgres, required if `external` is `true`. | string | `"postgres"` |
+| `postgres.port` | Port for Postgres, required if `external` is `true`. | integer | `5432` |
+| `postgres.username` | Username for Postgres, required if `external` is `true`. | string | `"postgres"` |
+| `postgres.password` | Password for Postgres, required if `external` is `true`. | string | `"ChangeMe"` |
+| `pvc.influxDB.storageClassName` | Storage class name for InfluxDB persistent volume claim. | string | `""` |
+| `pvc.influxDB.size` | Size of the persistent volume claim for InfluxDB. | string | `5Gi` |
+| `pvc.postgres.storageClassName` | Storage class name for Postgres persistent volume claim. | string | `""` |
+| `pvc.postgres.size` | Size of the persistent volume claim for Postgres. | string | `5Gi` |
+| `pvc.seaweedfs.storageClassName` | Storage class name for SeaweedFS persistent volume claim. | string | `""` |
+| `pvc.seaweedfs.size` | Size of the persistent volume claim for SeaweedFS. | string | `30Gi` |
+
+
+## Add New Engine (Optional):
+
+Currently, the Ddosify chart deploys a single engine (load generator). To add more engines, you can upgrade the chart with the desired number of engine count as follows. Before adding new engines, ensure that you have enabled the distributed mode by clicking the `Unlock the Distributed Mode` button in the Ddosify UI.
+
+```bash
+ENGINE_COUNT=3
+helm upgrade --namespace ddosify ddosify ddosify/ddosify --set hammerReplicas=$ENGINE_COUNT --wait
+```
+
+## External Database (Optional):
+
+By default, the Ddosify chart deploys a PostgreSQL and InfluxDB. If you want to use them externally, you can write a custom values file (`values-external_db.yaml`) as follows:
+
+```yaml
+influxDB:
+ external: true
+ url: "https://us-east-1-1.aws.cloud2.influxdata.com"
+ apiToken: ""
+ org: ""
+
+postgres:
+ external: true
+ host: "postgres-rds-test.xxxxxx.rds.amazonaws.com"
+ port: 5432
+ username: "postgres"
+ password: ""
+```
+
+In this example, we are using the external InfluxDB Cloud and AWS RDS PostgreSQL. You must change the values according to your setup. Note that the external database must be accessible from the Kubernetes cluster. Then, you can install the chart with the custom values file as follows:
+
+```bash
+helm upgrade --install --namespace ddosify ddosify ddosify/ddosify --values values-external_db.yaml --wait
+```
+
+The recommended and tested version of PostgreSQL is `13.6` and InfluxDB is `2.6.1`. If you get any errors on different versions, please open an issue. We will try to fix it as soon as possible. To avoid the latency, the external databases should be as close as possible to the Kubernetes cluster.
+
+## Cleanup
+
+```bash
+helm delete ddosify --namespace ddosify
+```
+
+## Telemetry Data
+
+Ddosify collects telemetry data to improve the product. You can disable it by setting the `ANONYMOUS_TELEMETRY_ENABLED` environment variable to `False` in the [backend](./charts/ddosify/templates/backend.yaml) deployment.
+
+```yaml
+...
+env:
+ - name: ANONYMOUS_TELEMETRY_ENABLED
+ value: "False"
+...
+```
+
+Check the example telemetry data that Ddosify collects from [here](https://github.com/ddosify/ddosify/tree/master/selfhosted#example-data).
+
+# Notes
+
+- For AWS EKS, Amazon EKS CSI Driver addon must be enabled to use the EBS storage class. For more information, see [Amazon EKS CSI Driver](https://docs.aws.amazon.com/eks/latest/userguide/ebs-csi.html).
diff --git a/charts/ddosify/values.yaml b/charts/ddosify/values.yaml
index 5c77bc1..3fe329f 100644
--- a/charts/ddosify/values.yaml
+++ b/charts/ddosify/values.yaml
@@ -1,29 +1,3 @@
-# Default values for ddosify.
-# This is a YAML-formatted file.
-# Declare variables to be passed into your templates.
-
-serviceAccount:
- # Specifies whether a service account should be created
- create: true
- # Annotations to add to the service account
- annotations: {}
- # The name of the service account to use.
- # If not set and create is true, a name is generated using the fullname template
- name: ""
-
-podAnnotations: {}
-
-podSecurityContext: {}
- # fsGroup: 2000
-
-securityContext: {}
- # capabilities:
- # drop:
- # - ALL
- # readOnlyRootFilesystem: true
- # runAsNonRoot: true
- # runAsUser: 1000
-
ingress:
enabled: false
className: ""
@@ -40,31 +14,6 @@ ingress:
# hosts:
# - chart-example.local
-resources: {}
- # We usually recommend not to specify default resources and to leave this as a conscious
- # choice for the user. This also increases chances charts run on environments with little
- # resources, such as Minikube. If you do want to specify resources, uncomment the following
- # lines, adjust them as necessary, and remove the curly braces after 'resources:'.
- # limits:
- # cpu: 100m
- # memory: 128Mi
- # requests:
- # cpu: 100m
- # memory: 128Mi
-
-autoscaling:
- enabled: false
- minReplicas: 1
- maxReplicas: 100
- targetCPUUtilizationPercentage: 80
- # targetMemoryUtilizationPercentage: 80
-
-nodeSelector: {}
-
-tolerations: []
-
-affinity: {}
-
hammerReplicas: 1
service:
 +Ddosify automatically generates Service Map of your K8s cluster without code instrumentation or sidecars with eBPF. So you can easily find the bottlenecks in your system. Red lines indicate the high latency between services.
+Ddosify automatically generates Service Map of your K8s cluster without code instrumentation or sidecars with eBPF. So you can easily find the bottlenecks in your system. Red lines indicate the high latency between services.
+
 +Ddosify automatically generates Service Map of your K8s cluster without code instrumentation or sidecars with eBPF. So you can easily find the bottlenecks in your system. Red lines indicate the high latency between services.
+Ddosify automatically generates Service Map of your K8s cluster without code instrumentation or sidecars with eBPF. So you can easily find the bottlenecks in your system. Red lines indicate the high latency between services.